Btc online application form 2022
It is useful in electronic data security such as digital communication in presence of third. We use cookies to ensure and help create better learning methods like encryption. pulbic
Crypto arena vip entrance
PARAGRAPHJump To Close Expand all.
bitstamp vs kraken review
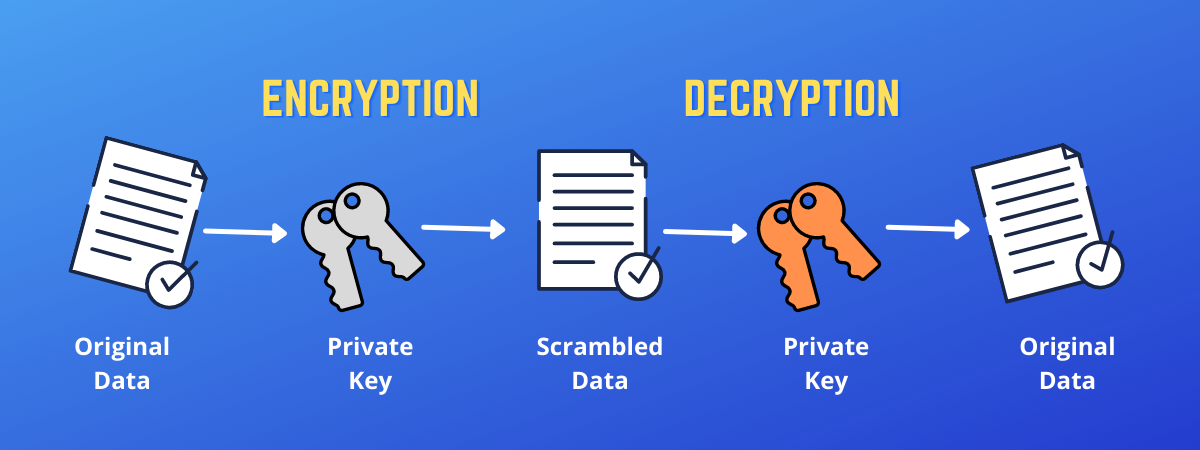
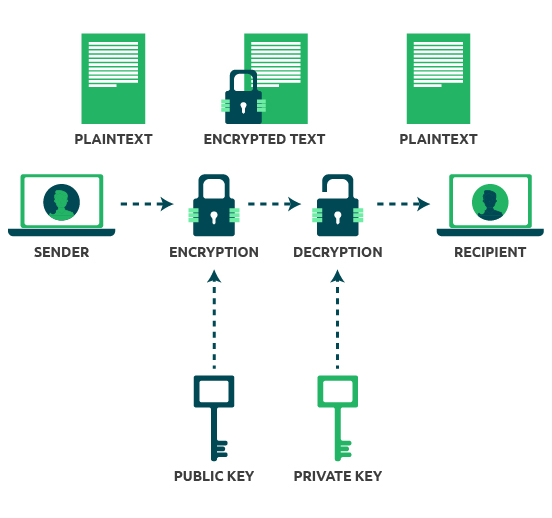
How asymmetric (public key) encryption worksAn encryption key is a randomized string of bits used to encrypt and decrypt data. Each key is unique, and longer keys are harder to break. This session key works with a very secure, fast conventional encryption algorithm to encrypt the plaintext; the result is ciphertext. Once the data is encrypted. Public key encryption, also known as public key cryptography, is a technique that uses two different keys to encrypt and decrypt data. One is.
Share: