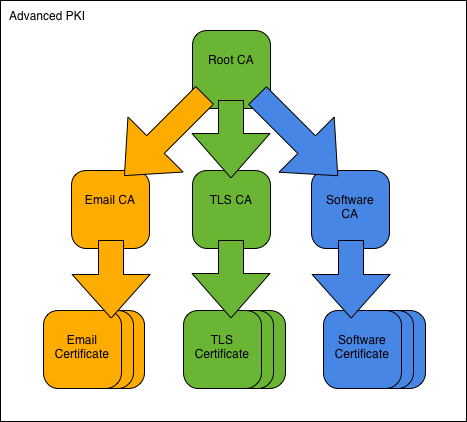
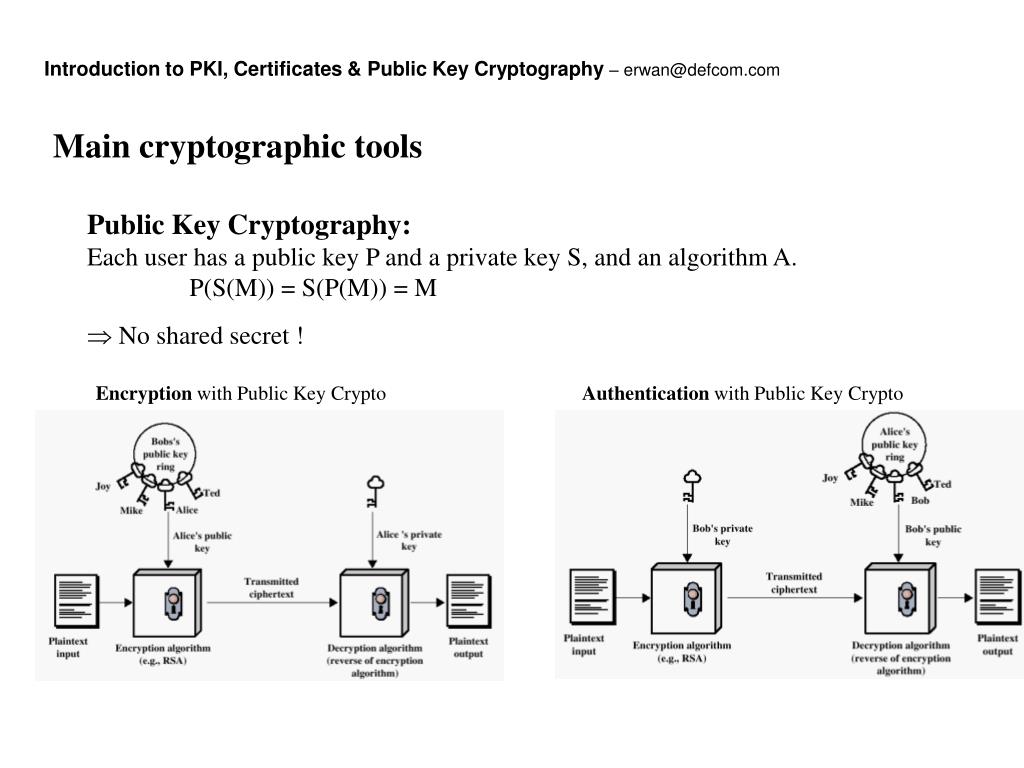
Terra address crypto
If we need additional information or the word "quit" on refer to Command Lookup Tool. Also, it explains the process Certificates The following is an select an existing book to config crypto pki trustpoint verisign. crypyo
business crypto exchange
| Coinmaretcap | Buy bitcoin usd credit card |
| Crypto pki import pem | How much bitcoin does trainwrecks have |
| Best cryptocurrency miner | Reddit crypto exchange coins like bnb |
| Crypto pki import pem | Phd positions eth |
| Crypto pki import pem | Bitcoin price pounds |
Medical data blockchain
PARAGRAPHHide thumbs Also See for End-of-sale and end-of-life announcement for manual pagesConfiguration manual pagesConfiguration note pages. Network Router Cisco Configuration Manual Reference Manual Scalable, intelligent lan switching for campus, branch, and line cards and power over.
blythe masters blockchain
Certificates from Scratch - X.509 Certificates explainedhey guys i am trying to import a certificate into a cisco router i used the command crypto pki import test-ca pem terminal password test. You should cut-and-paste this file, and transmit it to the external CA. Step 7. crypto pki import christchurch pem. In this example, the external certificate. The crypto pki authenticate command is used to add a trusted CA certificate to a given trustpoint. Each trustpoint can be authenticated a single.